Introduction
Understanding SharePoint Security Layers
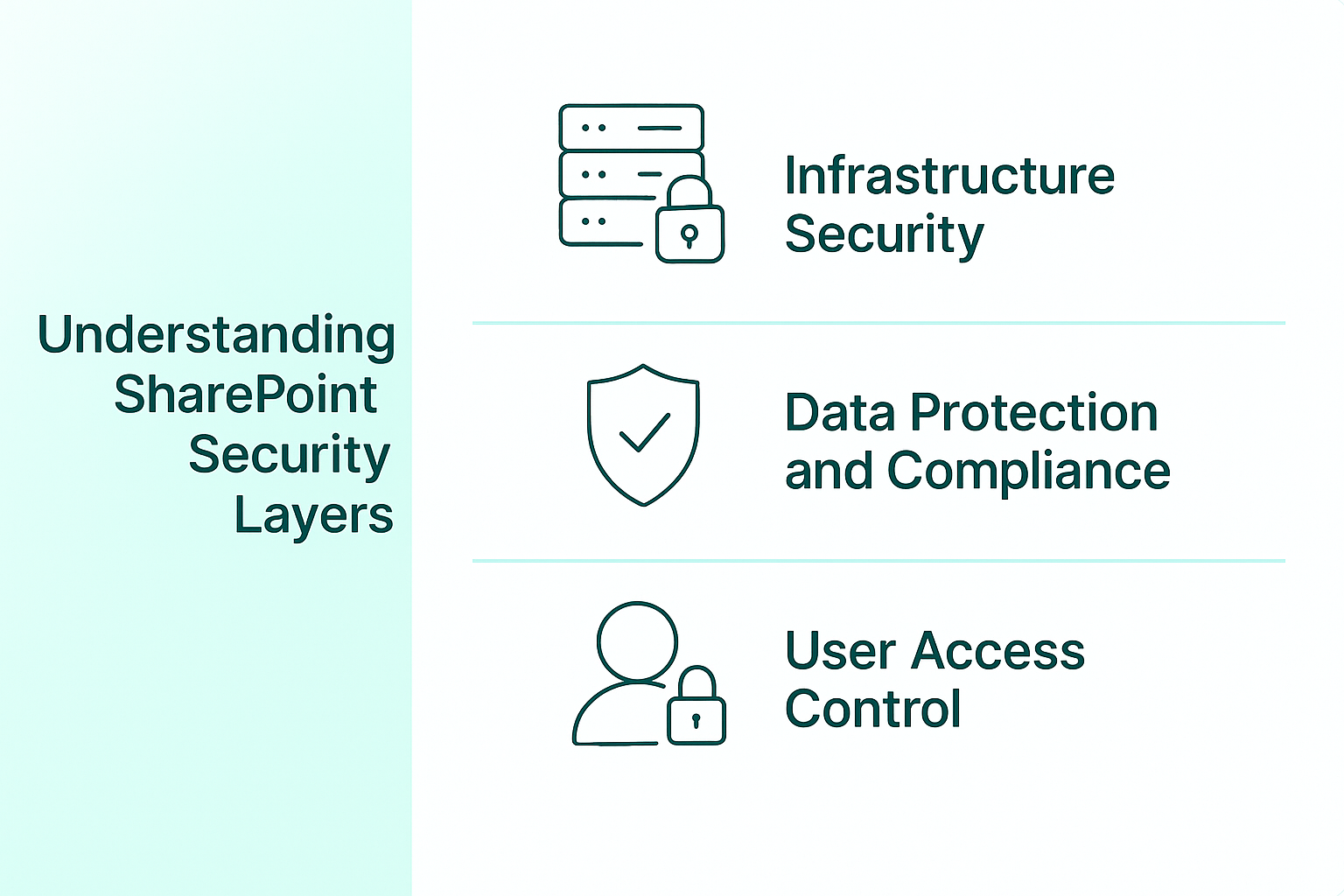
Infrastructure Security
- Physical security at Microsoft’s data centers includes security guards, video surveillance, and controlled access to protect the actual servers where your data lives.
- Network protection uses advanced firewalls and monitoring systems to block malicious traffic and prevent attacks like DDoS (where hackers try to overwhelm your systems).
- Server security involves regular security testing, keeping systems updated with patches, and hardened configurations that remove unnecessary features that could be exploited.
- Encryption in transit ensures that when data moves between locations, it’s encrypted using protocols like TLS 1.2 so it can’t be intercepted.
- Customer isolation keeps different companies’ data separate from each other in Microsoft’s cloud environment.
Data Protection and Compliance
- Data Loss Prevention (DLP) automatically finds and protects sensitive information like credit card numbers or personal data by scanning content and enforcing rules you create.
- Information Rights Management adds protection that stays with documents even after they’re downloaded, preventing unauthorized sharing.
- Retention policies let you automatically keep important records for required periods and safely delete data when it’s no longer needed.
- eDiscovery tools help you find specific information when needed for legal purposes.
- Compliance features help meet regulatory requirements like GDPR (European privacy law), HIPAA (healthcare privacy), and other industry standards
User Access Control
- Authentication systems verify users’ identities, preferably using multi-factor authentication for extra security
- Permission levels create a hierarchy of access:
- Site collection administrators (highest level access)
- Site owners (can manage specific sites)
- Contributors (can add and edit content)
- Viewers (can only read content)
- Administrator protections provide extra security for accounts with high-level privileges.
- External sharing settings control how and when content can be shared with people outside your organization.
- Conditional access makes security decisions based on factors like location, device, and risk level
Top 10 SharePoint Security Best Practices for 2025
1. Enforce Multi-Factor Authentication (MFA)
Steps to implement:
- Go to Microsoft 365 Admin Center > Users > Active Users
- Click on “Multi-factor authentication”
- Enable MFA for every account, especially global admins
Best Practice: Make MFA mandatory for everyone—internal staff, external collaborators, and admins No exceptions.
2. Conduct Permission Audits—Not Once, But Regularly
Audit to identify:
- Orphaned accounts (e.g., employees who have left)
- Users with excessive or irrelevant access
- External users who no longer need access
Tools to help:
- SharePoint’s native Site Permissions page
- Third-party tools: ShareGate, AvePoint, SysKit
Frequency:
- Quarterly comprehensive audits
- Monthly spot-checks for sensitive or high-risk sites
3. Deploy Microsoft Defender for Office 365
What it includes:
- Safe Attachments: Scans files for malware before delivery
- Safe Links: Evaluates link safety at click time
- Anti-phishing: Blocks spoofing and impersonation attacks
- Threat Explorer: Provides detailed threat investigation tools
4. Set Up Data Loss Prevention (DLP) Policies
Steps to implement DLP:
- Identify sensitive data categories: HR data, legal docs, IP, etc.
- Create custom information types as needed
- Define rules to alert, block, or encrypt based on severity
- Test policies to reduce false positives before full deployment
5. Use Conditional Access for Context-Aware Controls
What to consider:
- User role: Executives vs general staff
- Device state: Is it compliant and secure?
- Location: Trusted vs untrusted IPs or geographies
- Sign-in behavior: Risky patterns or unusual access

Sample policies:
- Restrict access to managed devices only
- Block downloads on personal or unmanaged devices
- Limit access from international or high-risk regions
6. Monitor Security Alerts and Act Swiftly
Steps to strengthen monitoring:
- Use Microsoft 365 Security Center for unified monitoring.
- Set automated workflows using Power Automate or Logic Apps.
- Deploy SIEM tools (e.g., Azure Sentinel) for real-time analysis.
- Maintain an incident response plan: define steps, roles, and simulate scenarios.
7. Invest in User Training and Awareness
Training topics to cover:
- Spotting phishing and suspicious emails.
- Handling confidential files correctly.
- Sharing responsibly with colleagues and guests.
- Reporting potential security issues promptly.
Extras:
- Customize training based on user role.
- Run quarterly phishing simulations to gauge readiness.
8. Control External Sharing and Guest Access
Best practices:
- Limit sharing to specific domains or trusted users.
- Require sign-in for guests—no anonymous links.
- Set expiration dates on all shared links.
- Monitor external access via reports monthly.
9. Have a Backup Strategy—Don’t Rely on Recycle Bin
Risks without backup:
- Limited retention (30–93 days)
- No full site/library restoration
- No point-in-time recovery for granular content
Recommendation:
- Use enterprise-grade backup tools (e.g., Veeam, Acronis):
- Restore down to single items or full sites
- Retain data long term for compliance
- Cover SharePoint, Teams, and OneDrive holistically
10. Stay Up-to-Date with Security Patches and Updates
- Updating SPFx solutions, apps, and web parts.
- Ensuring endpoints have the latest OS and browser patches.
- Tracking new features on Microsoft 365 Roadmap.
- Monitoring Message Center announcements.
- Updating hybrid/on-prem components.
Have a patching plan:
- Test patches in a dev environment.
- Roll out in controlled stages.
- Track deployment success and failures.
Common SharePoint Security Mistakes to Avoid

Over-permissioning Users
Neglecting Regular Audits
Establish a consistent audit schedule: monthly reviews of highly privileged accounts quarterly evaluations of general permissions and sharing settings bi-annual comprehensive security assessments, and event-driven audits following organizational changes. Automated auditing tools can reduce the administrative burden while improving consistency and coverage.
Ignoring Alerts and Notifications
Alert fatigue represents a serious security risk. When teams receive dozens of notifications daily critical warnings often get overlooked amid the noise, leaving your environment vulnerable even when warning signs are present.
Fine-tune your alert thresholds to reduce false positives implement alert categorization and prioritization, establish clear escalation paths for different alert types and document response procedures for common scenarios. For larger environments, consider implementing a security orchestration and automated response (SOAR) solution.
Misconfiguration of Sharing Policies
SharePoint’s powerful sharing capabilities often become its greatest security vulnerability when improperly configured. Common mistakes include allowing “Anyone” links by default, not setting appropriate link expiration periods failing to restrict file download capabilities and maintaining inconsistent sharing settings across site collections.
Set default sharing links to “Specific people” limit external sharing to authenticated users where possible enable link expiration for all sharing types apply file download restrictions for sensitive content and regularly review externally shared content.
FAQ’s
Conclusion
As cyber threats continue to evolve in sophistication and scale, a proactive and comprehensive approach to SharePoint security has never been more critical. By implementing the layered security practices outlined in this guide organisations can protect their valuable information assets while enabling the collaboration capabilities that drive modern business success.
Remember that security is not a destination but a journey requiring ongoing attention and refinement. Regular assessments user education and staying current with emerging security capabilities are essential components of an effective SharePoint security strategy.